Cybersecurity threats continue to evolve rapidly, with 2025 witnessing a surge in sophisticated cyber attacks targeting various sectors worldwide. This article delves into the prevalent types of cyber attacks, recent high-profile incidents, and strategies to mitigate these threats.
Understanding Cyber Attacks
A cyber attack is a malicious attempt to disrupt, damage, or gain unauthorized access to computer systems, networks, or data. These attacks can lead to significant financial losses, reputational damage, and compromise of sensitive information.
Types of Cyber Attacks in 2025
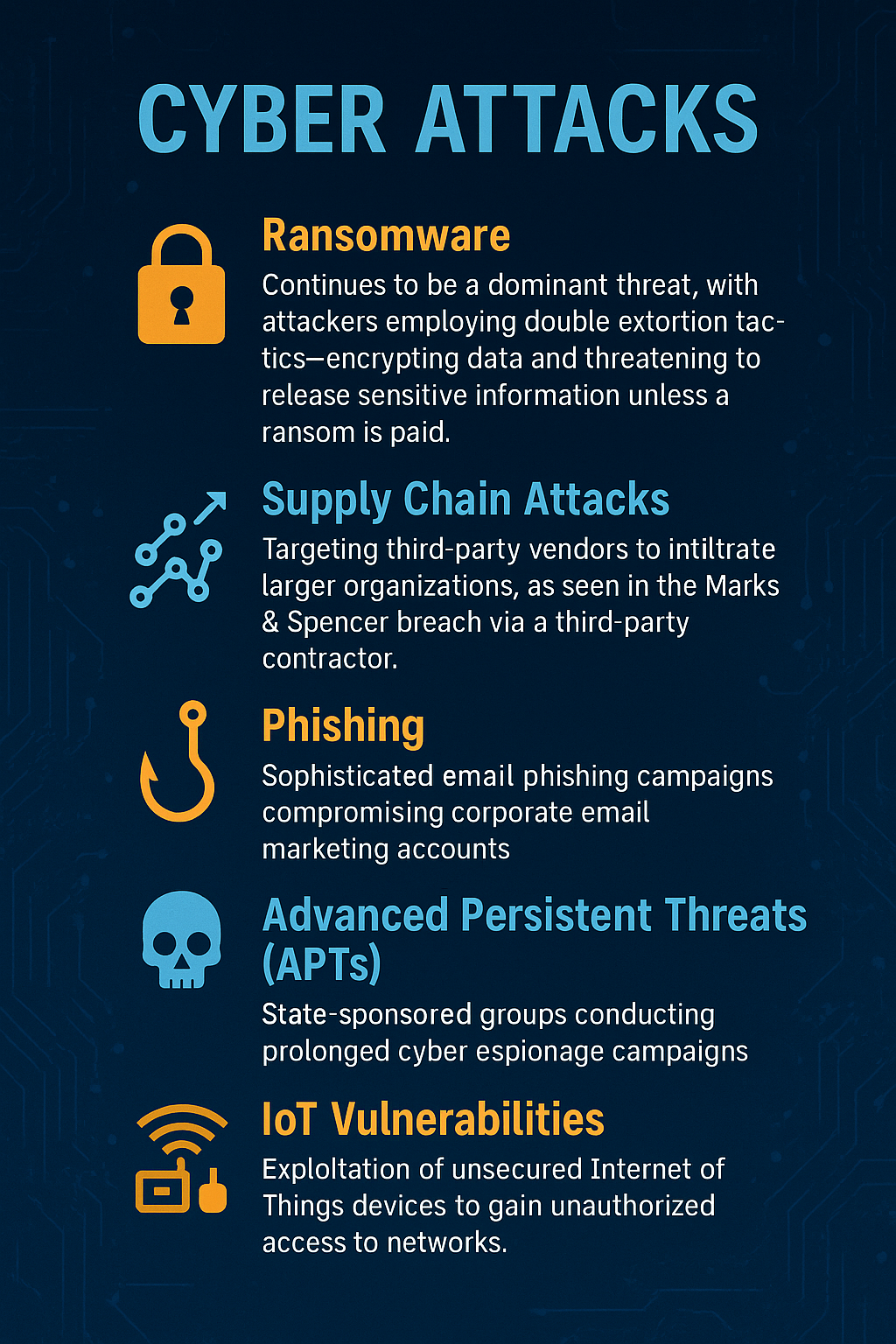
1. Supply Chain Attacks
Cybercriminals increasingly target third-party vendors to infiltrate larger organizations. By compromising a supplier’s system, attackers can gain access to the primary target’s network. This method was notably used in the SolarWinds attack, affecting numerous U.S. government agencies and corporations.
2. Ransomware Attacks
Ransomware involves encrypting a victim’s data and demanding payment for its release. The LockBit group, for instance, has been responsible for several high-profile ransomware attacks, including those on healthcare institutions and corporations.
3. Deepfake and AI-Powered Attacks
Advancements in artificial intelligence have enabled the creation of deepfake content—realistic but fake audio or video used to deceive individuals. Cybercriminals use deepfakes for impersonation, fraud, and spreading misinformation.
4. Advanced Persistent Threats (APTs)
APTs are prolonged and targeted cyber attacks where an intruder gains access to a network and remains undetected for an extended period. State-sponsored groups often employ APTs for espionage or sabotage.
5. IoT Vulnerabilities
The proliferation of Internet of Things (IoT) devices has expanded the attack surface for cybercriminals. Many IoT devices lack robust security measures, making them susceptible to breaches.
Recent Cyber Attacks in 2025
1. Marks & Spencer (M&S) Breach
In April 2025, UK retailer M&S suffered a significant cyber attack through a third-party contractor. The breach disrupted online operations and potentially exposed customer data. Investigations revealed that attackers exploited human vulnerabilities rather than technical flaws.
2. UK Legal Aid Agency Compromise
A cyber attack on the UK’s Legal Aid Agency compromised sensitive data of legal aid recipients and their lawyers. The breach led to the shutdown of online services to prevent further risks.
3. Peter Green Chilled Attack
Peter Green Chilled, a supplier to major UK supermarkets, faced a cyber attack where hackers demanded ransom. The incident raised concerns about the security of supply chains in the food industry.
4. Bank Sepah Data Breach
Iran’s Bank Sepah experienced a massive data breach, with hackers claiming access to over 42 million customer records. The attack highlighted vulnerabilities in the financial sector’s cybersecurity infrastructure.
5. SK Telecom Data Leak
South Korea’s SK Telecom disclosed a data breach affecting 23 million users. The company offered free SIM replacements and urged customers to enroll in protection services.
Mitigating Cyber Threats
To combat the growing threat of cyber attacks, organizations should:
- Implement Multi-Factor Authentication (MFA): Adding layers of security can prevent unauthorized access.
- Regularly Update Systems: Keeping software and systems up-to-date patches known vulnerabilities.
- Conduct Employee Training: Educating staff about phishing and other social engineering tactics reduces the risk of human error.
- Develop Incident Response Plans: Having a clear plan ensures swift action during a cyber incident.
- Invest in Advanced Security Solutions: Utilizing AI-driven security tools can detect and respond to threats in real-time.
Conclusion
The landscape of cyber threats in 2025 underscores the need for heightened vigilance and proactive measures. By understanding the types of cyber attacks and learning from recent incidents, organizations can bolster their defenses and protect against potential breaches.









Leave a Reply